Characteristics of Information
All good information has the characteristics discussed below,
1. Subjective: The value and usefulness of information are highly subjective, because whet is information for one person may not be for another.
2. Relevance: Information is good only if it is relevant - that is, pertinent and meaningful to the decision maker.
3. Timeliness: Information must be delivered at the right time and the right place to the right person. Example, if the manager gets information about the causes of machine failure a year after requesting it, the information is not timely and hence is probably not useful.
4. Accuracy: Information must be free of errors, because erroneous information can result in poor decisions and erode the confidence of users.
5. Correct Information Format: Information must be in the right format to be useful to the decision maker.
6. Completeness: Information is said to be complete if the decision maker can satisfactorily solve the problem at hand using that information. Although completeness of information is highly desirable, often complete information is not available.
7. Accessibility: Information is useless if it is not readily accessible to decision makers, in the desired format, when it is needed.
The Process of Converting Data into Information
The steps in this process may include the following:
1. Collecting.
2. Classification.
3. Sorting, adding, merging and so on.
4. Summarizing
5. Storing.
6. Retrieval.
7. Dissemination.
Why Organization Need Information System
Meeting Global Challenging:
Capturing Opportunities in the Market-Place:
Supporting Corporate Strategies:
Linking Departments whose Functions are Different:
Enhancing Workers Productivity:
Increasing the Quality of Goods and Services:
Potential Risks of Information Systems (IS)
"Deskilling" of Workers: Introduction of new technologies, especially for purposes of automation, sometimes render obsolete the existing skills of some workers.
Information Overload: Today, as information systems become more sophisticated and user-friendly, reports can be generated easily and quickly. But sometimes, managers who digest it and use it to make decisions, a phenomenon called information overload.
Employee Mistrust: When organizations introduce information systems, employees sometimes fear that computers will eventually replace them. Further, some companies use computers to monitor the activities of employees, which may also mistrust and dislike of computer.
Increasing Competitive Pressure: A few years ago, when computers were expensive, many companies (small businesses in particularly) that could not afford to invest in these machines found them-selves slowly and steadily being pushed out of the marketplace by large companies that invested heavily in computers and information systems. But now these technologies are very available with low priced. So most companies can use computers effectively to solve problems may be very successful; those that cannot may find themselves pushed out o the market by competitors that are more technologically sophisticated.
Disenchantment with IS: In recent years, the CEOs of many corporations have become disenchanted with computers and information systems because of poor returns from investments in these system. Through there can be many reasons for this, including investments in inappropriate technologies or poor applications of good technologies, poor returns can obscure the true value of computers and information systems.
Challenges in Developing Information System: Although there are many successive information systems, building these systems is one of the most difficult and challenging tasks facing IS personnel.
Security Breaches: When companies introduce new and sophisticated technologies, they must also find new ways to protect these assets from pilferage and security breaches.
System Components
Types of Information System
There are four types of information system:
i. Transaction Processing Systems - TPS.
ii. Management Information Systems - MIS.
iii. Intelligent Support Systems - ISS, included:
a) Decision Support Systems - DSS.
b) Executive Information Systems - EIS.
c) Artificial Intelligence and Expert System - ES.
iv. Office Automation Systems - OAS.
Transaction Processing Systems: TPS were among the earliest computerized systems. Their primary purpose is to record, process, validate and store transactions that take place in the various functional areas of a business for future retrieval and use. The six steps in processing a transaction are given below:
1. Data Entry: To be processed, transaction data must first be entered into the system. There are a number of input devices for entering data, including the keyboard and mouse.
2. Data Validation: Data validation is an essential step in transaction processing. It ensures the accuracy and reliability of data by comparing actual data with predetermined standards or known results. There are two steps in validation: error detection and error correction.
3. Processing and Revalidation: Once the accuracy and reliability of the data are validated, the data ready for processing. There are two ways to process transaction: Online and batch mode.
Online transaction processing (OLTP) - It is almost instantaneous processing of data. The term online means that the data input devices is directly linked to the TPS and therefore the data are processed as soon as it is entered into the system. The input devices may be at a remote location and be linked to the system by networks or by telecommunications system.
Batch processing - in which transaction are accumulated over time and processed periodically. Batch processing may be done on a daily, weekly, or monthly, or any other time period appropriate to the given application. For a example, a company may process the travel expenditures of the employees on a monthly basis, whereas sales may be processed at the end of each day.
4. Storage: Processed data must be carefully and properly stored for future use. Data Stored is a critical consideration for many organization because the value and usefulness of data diminish if data are not properly stored.
5. Output Generation: Once data has been input, validated, processed further, either to generate additional information or to present the same information in a different format. Some, examples of documents are invoices, paychecks, purchase invoices, sales receipts and job orders. Whereas a report is a summary of two and more transactions.
Computer output need not always be presented in hard-copy form, but can also appear on computer screens and panels. Such as soft-copy presentations are known as forms.
6. Query Support: The last step in processing a transaction is querying (asking questions) the system. Query facilities allow users to access data and information that may otherwise not be readily available. For example, a sales manager may query the system for the number of damaged items in a given store.
Management Information Systems: MIS are general-purpose, well-integrated systems that monitor and control the internal operations of an organization. They provide middle managers with vital information necessary to make tactical decisions and to assess the impact of daily operations on the long-range goals of the company.
The input to an MIS comes primarily from TPS and other sources within the company. The output of an MIS takes the form of summary reports and exception reports. A summary report accumulates data from several transactions and presents the results in condensed form. For example, a bank manager may get a summary report listing the total dollar amounts of deposits and withdrawals made the previous day. An exception report is a report that outlines any deviations from excepted output. The primary purpose of an exception report is to draw the attention of middle managers to any significant differences between actual performance and expected performance.
Intelligent Support Systems: ISS are systems that facilitates decision requiring the use of knowledge, intuition, experience and expertise. System that fall into this category are:
Decision Support Systems - DSS are interactive, well-integrated systems that provide managers with data, tools and models to facilitate semi-structured decisions or tactical decisions. A DSS accesses and processes large volumes of internal as external data and integrates them with various decision-making models. Internal data are often downloaded from the TPS or from other information systems. External data may come from a wide variety of sources. Such as external database maintained by government agencies or private companies.
The alternative generated by a decision maker can be further analyzed using "what-if" analysis which assesses the impact of changes made to input or output variables.
Executive Information Systems - A second type of ISS, used primarily by top management, is the EIS. It is a user-friendly, interactive system, designed to meet the information needs of top management engaged in long-range planning, crisis management and other strategic decisions. Strategic decision are unique, no repetitive and future oriented decisions which address long-term issue such as emerging markets, merger and acquisition strategies, new-product development and investment strategies. Such systems assist in the making of decisions that require an in-depth understanding of the firm and of the industry in which the firm operates.
Artificial Intelligence and Expert System - The third type of ISS is artificial intelligence (AI), a branch of computer science whose goal is to design and develop computer systems that emulate human intelligence. AI attempts to endow machines with capabilities and characteristics that would indicate intelligence if found in a human being.
Expert Systems (ES) are a branch of AI. These systems incorporate the knowledge and problem-solving skills of a human expert, such as a physician, a unclear scientist or an automotive engineer.
Office Automation Systems: These are systems that support the automation of various managerial and clerical activities. The primary goals of office automation are to enhance communication in the workplace and increasing the efficiency and productivity of knowledge workers and clerical workers. Office automation systems include:
Word Processing - Creating writing documents such as letters, memos and term papers, on the computer.
Desktop publishing - Using software with sophisticated publishing capabilities to create documents.
E-Mail - Sending mail electronically from one computer to other.
Voice mail - Storing, accessing, retrieving and distributing messages using the telephone.
Videoconferencing - Using group-oriented systems that allow users located in different parts of the world to engage in face-to-face communication.
Image retrieval and storage - Conversion of paper documents into electronic files and images for each retrieval and processing.
Facsimile Transmission, or fax - The transfer of written or pictorial information over phone lines to users anywhere in the world.
Electronic meeting systems - Systems that bring together people who are geo-graphically separated to facilitate face-to-face group meeting.
The Components Of a ComputerThe modern computer system consists of five basic components:
1. The central processor (central processing unit and primary storage).
2. Secondary storage.
3. Input devices.
4. Out put devices.
5. Communications devices.
The central processor:
The Central Processing Unit -
Primary Storage -
- Random Access Memory
- Read-Only Memory
- Cache Memory
- Register
Secondary storage:
Magnetic disk -
Floppy disk -
Hard disk -
Magnetic Tape -
CD-ROM -
Input devices:
Keyboard -
Mouse -
Touch Screen -
Voice Recognition -
Optical Character Reader (OCR) -
Magnetic Ink Character Recognition
Out put devices:
Video Display Terminals -
Printers - Dot matrix printer
Ink-Jet
Laser printer Sound Board -
Communications devices:
Types of ComputerComputer can be classified into different types based on memory size and processing speed. Those types of computer are explained below:
1. Supercomputer.
2. Mainframes.
3. Midrange Machines / Minicomputers.
4. Workstation.
5. Microcomputer or Personal Computer (PC).
6. Laptops and Notebooks.
7. Hand-Held Computers.
8. Pen-Based Computing.
Supercomputer:Supercomputers are the fastest and largest computers available today; they are used in a wide variety of applications. There are two features in every supercomputer. First feature, supercomputers have multiple processors (or CPUs) that process multiple instructions at a time, this is known as parallel processing. Second feature, fault-tolerant computers; a computer with a backup mechanism to automatically isolate and reconfigure hardware that fails during system operation.
Mainframes: A mainframe is a large, general-purpose computer with a large memory and excellent processing abilities. Mainframes, which are frequently organization wide systems, take their name from the “main frame” those applications, payroll, investment analysis, weather forecasting, airline reservations and other applications that require massive computations and large-scale processing. Unlike PCs, which serve only one user, mainframes serve many users at the same time.
Midrange Machines / Minicomputers:Minicomputers, which are typical work-group systems, are small yet powerful multi-user system with excellent memory capabilities and processing speeds.
Workstation:Workstations lie somewhere between midrange computers and PCs. They can be used by individuals or by groups. They are faster and more sophisticated than PCs and are equipped with a number of productivity tools that increase their efficiency. Advantages in microprocessors and sophisticated software have significantly increased the capabilities of these machines and today some workstations are handling tasks that ran on supercomputers and mainframes as little as 2 years ago.
Microcomputer or Personal Computer (PC):Microcomputers (also known as personal computer-PC) are regarded by many as one of the greatest inventions in history. Although the memory size and processing capabilities of microcomputers are less than those of mainframe, minicomputers, advantages in hardware technology have made the PC compact, powerful and versatile machine. When the components of a PC are customized to meet the particular information needs of the user, the process in called configuration. For example, a user may choose to have a system that has built-in fax capabilities, while another user may require a communication device, such as a modem, installed in the unit. In fact, “plug-and-play” is emerging as the central theme in computing today. The term refers to the ability of users to plug in different hardware and software components and customize their PCs to meet their own personal information needs.
Laptops and Notebooks:Laptops and notebook provide mobile computing technology. These computers are battery-operated and hence can be used any time and anywhere. Laptop computers are small enough to fit on the lap of a user; notebook computers are even smaller.
Hand-Held Computers:Hand-held computer are even smaller than notebooks. They are primarily used to collect field data. The New York City transit police use hand-help computers to apprehend criminals. When a suspect is apprehended, a police officer uses a hand-held computer to do a background check on the individual.
Pen-Based Computing:Pen-based computing refers to portable computers that use an electronic writing pad and a light-sensitive electronic pen, thus freeing users from the constraints of a keyboard.
Programming LanguageProgramming language is a computer language, with its own syntax and grammar which is used to write software.
Machine Language:Machine language, the first generation computer language, was tedious, error-prone and machine-dependent, that is programs written on one type of machine could not be executed on other types of machines without rewriting all the code.
Assemble Language:Assemble language, which uses meaningful abbreviations of works or mnemonics to represent basic computer instructions, emerged in the early 1950s. It is viewed as the second generation of computer languages.
High-Level Language:Between the mid-1950s and the 1970s, anew set of languages, called high-level language (HLL) or 3GLs (third generation languages), emerged. They were a big improvement over assembly language and machine language. 3GLs were English-like.
Very High-Level Language:Very high level language or 4GLs began to emerge in the late 1970s. They were designed primarily to overcome some of the limitations of high level languages. 4GLs are nonprocedural languages; in which the user need only specify what be done, not how it should be done.
Object Oriented Programming:Object Oriented Programming, also known as OOPs, is another kind of programming language that has become increasingly popular in recent years. It enhances the productivity of programmers and reduces software development time.
Here, each object includes programming code that specifies how it should behave, how it should manipulate data, respond to messages from other objects and send messages of its own. The principal benefit of OOPs is code reusability, which means that the same piece of code can be used for different applications.
Visual Programming:The term visual programming refers to programming languages that allow user to visualize their code and its impact on the system, thus helping them to create powerful and less error-prone applications in less time.
Types of SoftwareSoftware can be classified into two broad categories: system software and application software. System software performs computer-related tasks such as managing input and output devices. Application software performs people-related tasks, such as human resources and marketing.
1. System Software.
2. Application Software.
System Software:System software performs the basic functions necessary to start and operate a computer. It controls and monitors the various activities and resources of a computer and makes it easier and more efficient to use the computer. System software is classified into three categories:
i. System control software - Programs that manage systems resources and functions.
ii. System support software - Programs that support the execution of various applications.
iii. System development software - Programs that assist system developers in designing and developing information system.
Application Software:Application software is designed to perform people-related tasks such as payroll, inventory and sales analysis. The United Nations uses application software to meet its information needs. There are two types of application software.
i. General purpose - Designed for general applications, such as payroll and so on.
ii. Dedicated software - Designed for specific applications, such as the space shuttle.
Telecommunication ChannelsA channel is the part of the telecommunications system that constitutes the link between message source and message destination. Telecommunications channels are identified according to transmission rate, transmission mode, and transmission direction.
Transmission Rate:It is capacity of a telecommunications channels; it depends on the bandwidth, which is the difference between the highest and the lowest frequency carried over the channel. The greater the bandwidth, the more information can be transmitted simultaneously over the channel. Bandwidth can be classified into three groups:
1. Voice-band or Low Speed - Transmission rates vary between 300 bits per second (bps) and 9,600 bps.
2. Medium Speed - Transmission rates vary between 9,600 bps and 256,000 bps.
3. Broad-band High Speed - Transmission rates vary between 256,000 bps and to a very large number, usually in the billion.
1. Voice-band or Low Speed - Transmission rates vary between 300 bits per second (bps) and 9,600 bps.
2. Medium Speed - Transmission rates vary between 9,600 bps and 256,000 bps.
3. Broad-band High Speed - Transmission rates vary between 256,000 bps and to a very large number, usually in the billion.
Transmission Mode:It is the mode in which data are transmitted over the network. There are two modes: synchronous and asynchronous.
1. Synchronous - Synchronous transmission transmits a group of characters at a time.
2. Asynchronous - It transmits one character at a time.
1. Synchronous - Synchronous transmission transmits a group of characters at a time.
2. Asynchronous - It transmits one character at a time.
Transmission Direction:It is the direction in which data is transmitted. Transmission direction is categorized in three ways: simplex, half-duplex and full-duplex.
1. Simplex - In simplex mode, a data communication devices can either send or receive data, but cannot do both, so transmission occurs in one direction only. For example, television broadcasting which moves only from TV station to the TV set.
2. Half-duplex - In half-duplex mode, the sender and the receiver can alternate sending data. That means, when one party has completed a transmission, control of the channel switches to the other party, allowing it to transmit data. An example of a half-duplex devices is a walkie-talkie.
3. Full-duplex - In full-duplex mode, both parties can send and receive information at the same time. An example of a full-duplex device is the telephone, on which both parties can speak and be heard at the same time.
1. Simplex - In simplex mode, a data communication devices can either send or receive data, but cannot do both, so transmission occurs in one direction only. For example, television broadcasting which moves only from TV station to the TV set.
2. Half-duplex - In half-duplex mode, the sender and the receiver can alternate sending data. That means, when one party has completed a transmission, control of the channel switches to the other party, allowing it to transmit data. An example of a half-duplex devices is a walkie-talkie.
3. Full-duplex - In full-duplex mode, both parties can send and receive information at the same time. An example of a full-duplex device is the telephone, on which both parties can speak and be heard at the same time.
Telecommunications MediaTelecommunications Media are the links over which data are transmitted. There are two types of telecommunications media: bounded and unbounded.
Boundary Media:In a Boundary Media, the signals are confined to the medium; they never leave it. The tree most popular types of boundary media are "twisted-pair" wire, coaxial cable and fiber-optical cable.
1. Twisted pair - A twisted pair consists of two insulated stands of copper wire twisted together. An ordinary cable consists of a number of twisted pairs, grouped together and enclosed in a protective sheath. Twisted-pair cable is one of the most popular telecommunications media for phone lines and computer networks.
2. Coaxial Cable - Coaxial cable consists of a central conducting copper core surrounded first by a layer of insulating material and then by a second conducting layer of braided wire mesh. A layer of nonconductive insulation, called a jacket also covers the wire to make it weather-resistant and usable both on land and under water. Coaxial cable is extensively used in the cable television industry and over short distances in computer networks.
3. Fiber-Optical Cable - Fiber-optic cable consists of thousands of hair-thin stands of glass or plastic, called the core, bound together inside a glass cylinder, which is covered by a protective sheath known as the cladding. Fiber-optic cable carries signals in the form of modulated light beams. It has become very popular because it is smaller, lighter and faster than other two.
Unbounded Media:In an unbounded or wireless, medium, the signals are not confined to the medium. Wireless media propagate signals through the atmosphere, the ocean and outer space. Wireless communication makes a mobile office easier to implement, airline passengers can keep in touch with their offices through the use of wireless phone, fax, and e-mail services and can even access online information services from the air - or from anywhere. There are five types of wireless communication:
1. Microwave - Microwave radio is a popular unbounded medium that uses radio signals to transmit large volumes of voice and data traffic.
2. Communication Satellites - Communication Satellites are launched into geosynchronous orbits at an altitude of about 22,300 miles above the equator. Satellites are powered by solar panels. They carry a variety of signals, such as standard television broadcasting, telephone transmissions and even high-speed data.
3. Cellular Phone - Cellular phones are wireless personal telephones. A cellular system partitions geographical area into cells; each cell has a base station with a radio transmitter, a receiver, an antenna and a computer.
4. High-Frequency Radio Telephone - It uses radio waves to transmit information over great distances. High frequency signals radiate from an antenna using ground waves and sky waves.
1. Local Area Network (LAN) - A LAN is a network that links a number of independent electronic devices located within a moderate-sizes geographic area, usually with a radius 1 to 10 miles. LANs are used primarily to connect devices within buildings and offices so that knowledge workers can share data, information, messages, software and even peripherals such a printers. Hence a LAN is owned by a single organization.
2. Wide Area Network (WAN) - A WAN is a network that spans wide geographical areas, sometimes even countries for data and voice communications. The primary difference between a LAN; also, unlike a LAN, which is usually owned by a common or organization, a WAN is owned both by the organization and by a common or special-purpose carrier.
3. Metropolitan Area Network (MAN) - MANs are high-bandwidth WANs that link electronic devices distributed over a metropolitan area. They are used for LAN-to-LAN connections, high-speed data transmission, backup network facilities, full motion video and image transmission.
Network TopologiesTopology is the geometric configuration of devices on a network. There are three popular network topologies: bus topology, ring topology and star topology.
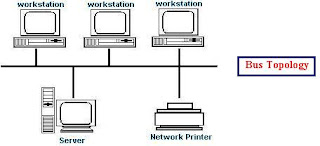
1. Bus Topology - Bus topology is the connection of all computers on the network through a simple circuit to a central channel or communication bus. Signals that are transmitted over the channel are called messages. Each message is transmitted to all the computers on the network, although only the targeted devices will respond to the message. Each devices has an address that is used by another devices to send messages to it.
The advantage of bus topology is that it is easy to add devices to the network or remove them without affecting network performance. Another advantage is that if one of the devices on the network fails, the network is not affected.
The disadvantage is that the performance of the network decreases as the number of messages increases, since each node has to check every message whether or not the message is address to it.
2. Ring Topology - Ring topology arranges the devices on the network in a circular array. Instead of relying on a host computer, the ring network transmits a message to all the nodes between the sending node and the receiving node. Each computer can communicate directly with any other computer on the network by specifying the address of the devices; the processing and control functions are distributed among all devices on the network. If a node fails, the message is rerouted around it.
3. Star Topology - With start topology, a central host computer receives messages and forwards them to various computers on the network. For one node to communicate with another node on the network, the central controller establishes a circuit, or dedicated path, between the two.
Open Systems Intercommunication (OSI)One of the most widely used network architectures is the open systems interconnection (OSI), developed by the International Standard Organization (ISO). The OSI is popular because it uses a seven-layered functional approach to achieve the primary goals of network architecture: modularity, simplicity, flexibility and openness.
Layer 7 : Application Layer - It deals with the software applications that we use on our screen. Layer 7 is concerned with file access and file transfer. If we have even used applications such as FTP or Telnet, we have interacted with as example of Layer 7.
Layer 6 : Presentation Layer - It deals with the way different systems represent data. For example, Layer 6 defines whet happens when it tries to display Unix-system data on an MS-DOS screen.
Layer 5 : Session Layer - It handles the order of data packets and bidirectional (two-way) communications. The session layer is to break a single large document into several smaller documents, packaging them and labeling the order in which the packages should be opened.
Layer 4 : Transport Layer - It is concerned with ensuring that mail gets to its destination. If a packet fails to get to its destination, Layer 4 handles the process of notifying the sender and requesting that another packet be sent.
Layer 3 : Network Layer - It provides an addressing scheme. If we send someone a letter, we use a street address that contains a ZIP code because that's what the post office understands. When a computer sends a data packet, it sends the packet to a logical address, which is like a street address.
Layer 2 : Data Link Layer - It, by contrast, isn't physical. This layer represents a set of rules governing the actual delivery of physical mail - pick up here, prop off there and so forth. This is where the rules for Ethernet, Token Ring, FDDI, ATM and so on are stored.
Layer 1 : Physical Layer - This layer is concerned only with the physical aspects of the network, the cards, wire and concentrators that move data packets.
Data Hierarchy
Methods for Organizing Data in FilesSequential File Organization
Direct File Organization
Indexed-Sequential File
Database Management SystemsDatabase Management Systems (DBMS) are support programs that work in conjunction with the operating system to create process, store, retrieve, control and manage data. The five primary functions of a DBMS are:
Function | Description |
Define, create and organize a database | Establish the logical relationships among different data elements in a database, define schemas, and sub schemas using the data definition language (DDL). |
Input data | Enter data into the database through an input device, such as a data screen, a touch screen, or a voice-activated system. |
Process data | Process and manipulate data using the data manipulation language (DML). |
Maintain data integrity and security | Limit database access to authorized users. |
Query database | Provide decision makers with information they need to make dependable decisions. Query the database using SQL. |
The Components of a DBMSData Definition Language
Data Manipulate Language
Data Dictionary
Database ModelsHierarchical Data Model
Network Model
Relational Model
Entity Relational Diagram
Distributed Databases
Client-Server Computer
Developing Client-Server Systems
Advantages of Client-Server Systems
Disadvantages of Client-Server Systems
Steps in Problem Solving
Decision Support System
Types of Problem
Components of a DSSDatabase Management Systems
Model Management Systems
Support Tools
Functions of DSS
Executive Information Systems
Characteristics of an EIS